As a Kamatera reseller, maintaining strict control over how your clients access their cloud resources is paramount for security. This article guides you through the process of assigning a specific security login protocol for each user account.
By defining the login protocol, you establish a critical layer of defense that secures your clients’ servers from unauthorized entry. Properly managing this setting ensures that access methods adhere to your security policies and the specific needs of your client’s technical environment.
Here’s how to do it:
- From the administrative panel on the left side of the screen select “Permissions” > “Users.”
- Select the user from the User Management list and click Edit, located in the bottom right corner of the User Information window.
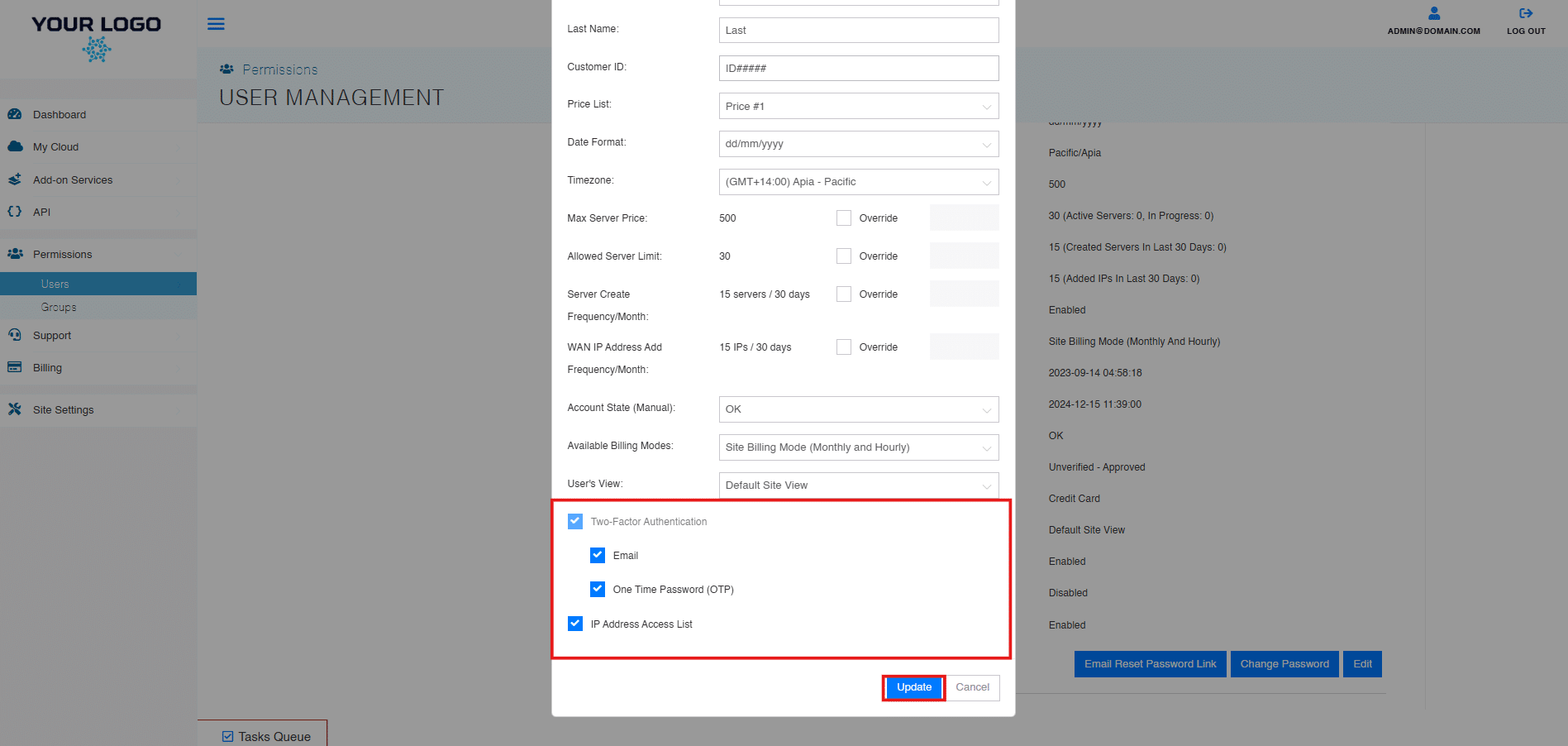
- The Edit User pop-up will appear. At the bottom of the pop-up, you will see two checkboxes, labelled “Two-Factor-Authentication” and “IP Address Access List.” Select your choices, then click Update when finished.
- The changes will now reflect in the User Info Tab within User Management.
You have successfully learned how to assign and manage a user’s Security Login Protocol. By precisely defining access methods, you ensure that all client server interactions align with your established security policies and best practices.
