Why the Client-Server Model Still Dominates (and When It Falls Flat)
Developers

When you check your bank balance on a mobile app, browse Instagram on your laptop, or order lunch to your office, you’re experiencing one of the internet’s most fundamental relationships: client-server architecture. This classic model is the unseen engine that powers our digital world, with a “client” (like your web browser) requesting information and a “server” (a powerful computer somewhere else) providing it. It’s a design that has defined an era of computing.
Client-server architecture comes with strengths that make it indispensable, and limitations that challenge its dominance. As edge computing, microservices, and peer-to-peer networks gain momentum, we take a look at how client-server architecture will evolve and where it still makes sense. Understanding these advantages and disadvantages is critical for anyone designing, managing, or simply trying to comprehend the digital infrastructure that runs our world.
What is client-server architecture?
Client-server architecture is a computing model that leverages a centralized server which receives and processes requests from multiple clients over a network. It is a commonly used architecture that supports various web-based, database, and enterprise applications.
A client-server architecture is constructed out of three core components.
Client: The client can be a device, such as a computer, tablet, or smartphone. Software, such as a web browser or mobile app, can also serve as the client. The client usually utilizes a user interface to handle input and output.
Server: The server is a centralized hardware or software system that receives and processes requests from the clients and returns responses. A single server can perform multiple functions, including storing data, hosting applications, and executing computing tasks requested by the client. Companies may host their servers on-premises or utilize cloud servers, which provide enhanced flexibility and scalability.
Network: The network provides the communication channel that serves as the client server connection. Organizations can use a local area network or the Internet as the client-server network. A reliable network connection is essential here.
How does client-server architecture work?
Client-server architecture utilizes a sequential series of four general steps.
- A client requests something from the server. The request can be for a variety of reasons, such as accessing a file, querying a database, or returning a webpage.
- The server receives the request and attempts to process it.
- The server sends a response to the client computer, ideally with the requested information.
- The client computer gets the data and displays it or uses it for further processing.
Teams typically implement a client-server architecture using a tiered methodology, based on the type and scope of the underlying application.
1-Tier: The client, server, and database are all resident on a single machine. This simple architecture eliminates the network component and is only suitable for basic desktop applications.
2-Tier: In this architecture, the client communicates directly with the server over a network. It is used for small applications and is not easily scaled to address evolving business requirements
3-Tier: In a 3-tiered architecture, the client interacts directly with an intermediary application server, which then communicates to a database server. Enterprise applications often use this architecture because it offers improved security and is scalable.
N-Tier: Large-scale enterprise and cloud-native applications may add multiple tiers to handle specific functions, such as data processing and performing analytics.
What are the advantages of client-server architecture?
Why do organizations choose client-server communication? Because it works. The clear separation between user interfaces and backend systems creates natural security boundaries and makes scaling straightforward. Whether powering network applications, mobile apps, or enterprise databases, client-server communication makes the most of your server resources.
Centralization
The server represents a centralized location for storing data and applications. This centralized control facilitates efficient system management and streamlines the work of IT administrators. For example, application updates only need to be applied to the server, not to all client devices, saving the IT team time.
The centralized nature of the client-server model ensures consistency for all clients. It can be very challenging to keep everyone on the same page and verify that a large user base has applied the necessary application updates to their devices. Centralization supports productivity by standardizing application access across the organization.
Scalability
One of the most appealing characteristics of the client-server model is the ease with which it can be scaled to handle fluctuating user traffic patterns or address business growth. IT teams can add or remove client users and devices without disrupting server functionality. Companies can upgrade the servers with additional resources to serve more clients with no performance degradation.
Scalability, however, is not limitless in the client-server model. Companies need to be aware of their computer networks’ limitations when scaling a client-server environment. At some point, adding more clients may degrade performance for all users, and the server itself might need to be replaced with a more powerful machine.
Enhanced security
Companies can enhance security by building applications that utilize the client-server architecture. The model preserves data integrity in multiple ways.
Organizations can implement strict access controls initiated at the server level. Security teams can enforce multi-factor authentication to keep unauthorized entities out of the system. Teams can conduct more effective monitoring and auditing of server-based resources to promote compliance and identify potential security vulnerabilities.
Companies can keep sensitive or high-value data on the server and control the ways clients can use it. Through this centralized data management, teams can place restrictions on downloading specific files so they are not resident on potentially exploitable client devices.
Businesses can enforce consistent access controls and data encryption to protect valuable resources from external and internal threat actors.
Maximizing resource utilization
Clients can access shared resources and peripheral devices either stored on or connected to the server. For example, a simple client-server environment in a small office enables all users to access the same printer and scanner, substantially reducing company expenses. Teams can reduce data duplication and operate more efficiently and consistently by sharing server-based databases and files rather than downloading and processing these resources on client devices.
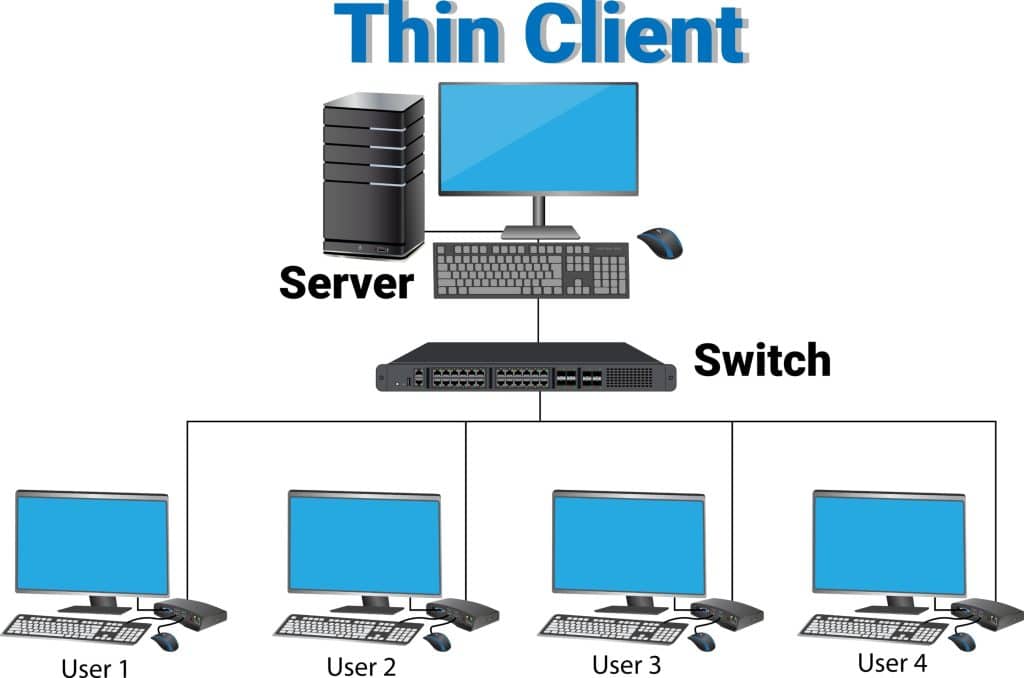
Reduced client requirements
This architecture lets you reduce the requirements on client devices, making them lightweight and cost-effective. Because the server handles the bulk of the processing and data storage, users can access powerful applications from virtually any device, including thin clients, older computers, or tablets. This also provides the benefit of centralized management, as IT teams can update, secure, and maintain applications in one central location, rather than on each individual client device. This simplifies administration and ensures a consistent user experience across the entire network.
Streamlined backup and disaster recovery
Organizations must take the necessary steps to protect their environment with reliable backups and a viable disaster recovery plan. The client-server model streamlines these efforts by providing a single target for backups, making it easier for teams to verify backup procedures are successfully protecting their data. Similarly, a disaster recovery plan only needs to be concerned with restoring the server and network access for the clients. Clients can implement recovery procedures tailored to their device type.
Role separation
The server-client model promotes improved organization when developing and resolving issues with an application. Servers handle storing and processing data and provide services to clients. The client only needs to be concerned with facilitating data input and output, as well as providing a user interface. Support teams can quickly identify the source of application issues for more timely problem resolution.
Concurrent access
In client-server architecture, web servers can handle concurrent access to resources and applications. The server responds to and manages simultaneous requests, ensuring consistency for all clients. This is crucial for e-commerce solutions, where the server must address client requests quickly to prevent customer dissatisfaction.
What are the disadvantages of client-server systems?
Organizations looking to adopt a client-server architecture must first navigate its potential pitfalls. The very nature of this model—where every action relies on a central hub—creates a single point of failure. A server crash can halt operations for all connected users, and a spike in client requests can overwhelm even robust remote servers, causing frustrating slowdowns or complete outages.
Single point of failure
The centralization that is an advantage of the model also presents the risk of a single point of failure. A crash or cyberattack on web servers affects all clients, making it impossible to access data or cloud services. This aspect of the architecture illustrates the importance of protecting the server with robust cybersecurity measures.
Initial cost
Implementing a client-server model can be a significant financial undertaking. The high initial costs for powerful server hardware, software licenses, and robust networking components can be a barrier for many businesses. Decision-makers must carefully weigh this investment against the long-term benefits, recognizing that this upfront expense is purchasing centralized computing power that can drive efficiency, scalability, and security for the entire organization.
Scalability limitations
Companies must be aware of the scalability limitations of their servers to maintain consistent and optimal performance for all clients. Servers can only support a finite number of clients, and exceeding this threshold can degrade application performance. Teams may need to resort to load balancers or consider adding more file servers to handle additional user requests.
Maintenance requirements
While client-server architecture offers the convenience of having all data stored centrally, it creates a dependency on a specialized team. A skilled IT team is crucial for network management, as they must perform all server updates, security patches, and performance-tuning to ensure the entire client base can rely on the server without disruption.
Security vulnerabilities
A centralized server provides an attractive target for threat actors. A successful cyberattack that brings down the server can affect business-critical systems and impact the ability to serve clients and customers. An attacker can gain access to the server from a compromised client, making it essential to implement strong authentication measures to safeguard the system.
Alternative IT architectures
Client-server architecture does not fit the computing needs of all organizations. A company’s network administrator may choose to meet its computing requirements with one of the following alternative IT architectures.
Peer-to-peer (P2P) architecture
In the peer to peer network model, each device, or peer, can act as a client and a server. There is no central server. Instead, every network node has equal capacity. Peers share resources directly with other devices. File-sharing networks and blockchain systems typically utilize a P2P architecture.
Advantages of the P2P model include:
- No central failure point
- Limitless scalability by adding more peers to the network
- Cost-effective by eliminating the need to maintain a centralized server
The P2P architecture also presents disadvantages, including:
- Inconsistent performance that relies on the capabilities of individual peers
- Complex management and security minimize the use of P2P for large or enterprise applications
Microservices architecture
This model breaks applications into small, independent services that communicate with each other through application programming interfaces (APIs). Teams can deploy and scale services independently, giving organizations greater control over application components. Modern web apps often utilize this architecture.
Advantages of microservices include:
- Development and deployment flexibility
- Enhanced issue isolation and resolution
- Support for agile development and DevOps best practices
Disadvantages of the microservices model are:
- Management complexity
- Increased operational overhead
- Requires orchestration with tools like Kubernetes
Cloud-based architecture
Companies using cloud computing may opt for a cloud-based architecture, which can be implemented by a serverless or function-as-a-service (FaaS) model. The application runs on cloud infrastructure, allowing developers to concentrate on the underlying code or services. Advantages of this approach include:
Organizations must be aware of potential drawbacks, including:
- Vendor lock-in with migration challenges
- Monitoring and debugging complexity
Edge computing architecture
The edge computing model moves data storage and processing to users and devices closer to the edge of the network. This approach reduces the dependence on a central server by assigning more responsibility to clients and edge devices. Internet of Things (IoT) and applications that require real-time processing can benefit from edge computing due to its reduced latency and bandwidth usage.
Disadvantages to this approach include the efficiency of using the limited computing resources of edge devices compared to a centralized server. It is also challenging to ensure data consistency and the security of edge devices. A compromised device may allow threat actors to gain access to the corporate network. Vendors use this architecture for applications such as smart home devices and self-driving vehicles.
Conclusion
The client-server architecture is a popular method of deploying computing resources that organizations can scale to address simple and complex applications. It is an essential component in supporting today’s mobile workforce, allowing individuals to interact with company resources via mobile devices. Companies that utilize this approach must focus on protecting the server to maintain its security and ensure availability to the client community.
Organizations should consider alternatives before implementing a client-server architecture to support an application. Failing to make the right choice will limit the benefits of the application, negatively impacting operational efficiency and the company’s bottom line. Decision-makers must choose the computing model that best supports their objectives and requirements.
